Application Areas for Device Security
Industrial: The US Department of Homeland Security is advising manufacturers of industrial control systems (ICS) and Supervisory Control and Data Acquisition (SCADA) to implement heightened security for their devices. The Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) has warned manufactures of programmable logic controllers (PLCs) that there are new publicly available exploit tools that specifically targets PLCs.
Medical: Medical device manufacturers need to protect the privacy of patient information and be concerned about malicious intrusions that could compromise the integrity of the device.
Consumer Electronics: The growing Internet of Things means more opportunities for hackers and cyber criminals to exploit consumer information.
Embedded Device Security Suite
Security for network-connected embedded devices is becoming a critical consideration for ODMs and OEMS. Organized crime, terrorist groups and nation states are spending millions of dollars preparing cyber attacks on embedded devices. These attacks will only increase in their intensity and sophistication.
The embedded security solutions from Quadros systems are focused on four areas:
Embedded Firewall
Network-connected embedded devices are vulnerable to the same kinds of attacks prevalent in the desktop and server world. These attacks can range from amateur hackers to industrial espionage to terrorism.
Quadros Systems has partnered with Icon Labs to provide a new layer of robust network security for embedded systems. The system is designed explicitly for use in embedded devices with limited memory and processor speeds that require secure network implementation certified to standards such as the ISASP 99 which is measured by the Wurldtech Achilles® Test Platform.
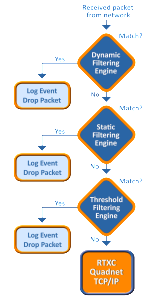
When integrated with the RTXC Quadnet TCP/IP stack, the Floodgate Packet Filter™ Firewall offers protection against intrusion, malformed packets, Denial of Service (DoS), storms, and other cyber threats.
Lockdown Mode for security critical applications. In Lockdown Mode all communication must originate from the embedded device; any communication originating from the Internet is blocked. Support is provided for a trusted devices list that can initiate communication.
- Provides the highest level of protection
- Protects against IP spoofing
- Can be used in combination with rules based filtering to further control the packets processed by the device
Static filtering blocks incoming packets based on configurable filtering rules.
- Easily configured rules
- White- and black list filtering
- Source IP address filtering
- Protocol filtering
- MAC address filtering
- Port filtering
Stateful Packet Inspection (also called dynamic filtering) filters packets based on the state of the connection. Offers faster performance and simplified filtering rules
- Configuration of filtering options
- IP header options
- TCP flags
- Configurable Time-to-Live (TTL)
Threshold-based Filtering blocks packets in real time based on based on network traffic pattern. Floodgate analyzes traffic patterns in real-time and performs filtering based on this data. When network traffic patterns exceed the configured thresholds packets are dropped to protect the device.
Application Layer Security – SSL/TLS
Secure Sockets Layer (SSL 3.0) and Transport Layer Security (TLS 1.0) are used to protect data passed between client and server at the application layer. In the desktop world you would use HTTPS for a secure connection to your financial institution. The same security can be used in embedded devices. SSL/TLS allows an SSL-enabled server to authenticate itself to an SSL-enabled client and, if necessary, allows the client to authenticate itself to the server. After the authentication and cryptology parameter negotiation, a secure channel is established so that the client and server can exchange information in a secure way.
- Small code size.
- Supports both SSL client and SSL server
- Mutual authentication with certificates
- Security for HTTP, FTP, SMTP and Telnet
- Configurable support for
- exportable cipher suites
- SSL 3.0, TLS1.0 or both
- SSL server, SSL client or both
- RSA and Ephemeral Diffie-Hellman key exchange method
- DSS signature algorithm
- Mutual authentication
- parsing SSL 2.0 client hello
- Support for resumed handshake, user determines the cache size.
- SSL Secure Renegotiation Support
- Supports exportable cipher suites (40-bit encryption), as well as strong encryption
- Cipher suites supported
- DHE (Diffe-Helman)
- AES (Advanced Encryption Standard)
- DES (Data Encryption Standard)
- 3DES (3 64-bit DES keys)
- DES40 (40-bit DES keys)
- R2C (RSA security)
- RC4 and AR
IPsec/IKE
Internet Protocol Security (IPsec) and Internet Key Exchange (IKE) is a method of providing security at the IP layer which means that each packet is encrypted. IKE is used for authentication and key exchange.
IPsec uses two protocols to provide traffic security – Authentication Header (AH) and Encapsulating Security Payload (ESP). AH and ESP may run in either transport mode or tunnel mode.
Quadnet AH
- Supports HMAC-MD5-96 and HMAC-SHA1-96, HMAC-RIPEMD160-96 and NULL authentication algorithm
- Tunnel and transport mode
- Nested tunnel
- Security Association (SA) bundle with Encapsulated Security Payload (ESP)
- Easy to add or remove algorithms
- Supports both IPv4 and IPv6.
Quadnet ESP
- Encryption supports
- NULL, DES, 3DES (Both DES and 3DES has configurable weak key checking and parity bit checking),
- BLOWFISH (key size 40-448 bits), CAST128 (key size 40-128 bits), RC5 (key size 40-2040 bits), IDEA (key size 128 bits), AES (RIJNDAEL, key size 128, 192, 256 bits), TWOFISH (key size 128,192, 256 bits) algorithm and in CBC mode. RC5 and IDEA algorithms require patent license.
- SHA256, HMAC-MD5-96, HMAC-SHA1-96, HMAC-RIPEMD160-96 and NULL authentication algorithm
- Tunnel and transport mode
- Nested tunnel
- Security Association (SA) bundle with AH
- Minimum padding
- Easy to add or remove algorithms
- Support for IPv4 and IPv6
Quadnet IKE
- Main mode, aggressive mode, and quick mode.
- Pre-shared Key,DSA and RSA signatures authentication methods
- Diffie-Hellman predefined group 1, 2 and 5.
- ID types – IPv4 and IPv6 Address, Subnet and Range, FQDN, USER_FQDN, and ASN1_DN
- Encryption algorithm DES, 3DES, BLOWFISH, CAST, AES (RIJNDAEL) and TWOFISH. Note: User needs to get RC5-R16-B64 and IDEA patent license before acquiring source code.
- Supports Perfect Forward Secrecy. If Quadnet IKE is the initiator for phase two, it always uses the phase one Diffie-Hellman group as the PFS proposal. If Quadnet IKE is the responder, it accepts group 1, 2 or 5.
- Supports Hash algorithms MD5, SHA1 and RIPEMD. The corresponding HMAC version hash algorithm is used as the Pseudo Random Function.
- Ignores commit bit and auth-only bit based on IKE bake-offs. Uses pre-setup incoming SA to avoid losing packet. Unique message ID list is maintained to work against replay.
- Cookie is generated using continuously refreshing secret key. Cookie verification is configurable.
- Lifetime is based on time and kilobytes.
- New group mode is not supported.
- Supports ISAKMP Informational Exchanges, including including DELETE, INITIAL-CONTACT message. Other informational messages will be silently discarded. (RFC states we MAY send an error notification.) We do not send RESPONDER_LIFETIME exchange because any participant may choose to renegotiate at its preferred time.
- One SA negotiation at each quick mode exchange
- For the pair exchanges, the requester is responsible for retransmit. The responder will retransmit only upon receiving a retransmitted message from the requester.
- Supports both IPv4 and IPv6.
- Packets are queued when negotiating SA, while time and bytes limitation apply.
- Once connection is established, Quadnet IKE will try to keep continuous channel between peers. Phase 1 ISAKMP SA will be automatically rekeyed once expires.
Recent enhancements
- Multiple phase 2 proposals
- Enhanced bundle processing
- IPsec policy opaque data support
Achilles Certification Consulting
The Achilles test suite from Wurldtech is a popular way to verify that your systems are safe from a variety of attacks including packet floods, port scanning, and spoofing.
Quadros Systems is experienced in working with this test suite and in hardening the network interfaces and application. We have successfully helped our customers using our software pass Achilles level 1 and level 2 tests.